Apr 29, 2020 A computer's hardware configuration determines its MAC address, while the configuration of the network it is connected to determines its IP address. However, if the computers are connected to the same TCP/IP network, you can determine the MAC address through a technology called ARP (Address Resolution Protocol), which is included with TCP/IP. Mar 06, 2020 Mac-binding essentially means binding together the MAC and IP addresses, so that all requests from that IP address are served only by the computer having that particular MAC address. In effect, it means that if the IP address or the MAC address.
That’s why having a clear map of your IP address space enables you to identify your network parts quickly, and at the same time helps you manage the whole network in a more efficient way.
For security researchers, it’s the starting point of identifying potential vulnerable sub-networks and IP addresses, for performing deep reconnaissance tasks such as OS and service scanning, vulnerability scanning, and more.
That’s why today we’ll show you the top 10 IP scanner tools for better network management and IP address discovery-mapping.
7 Best IP scanner tools
Let’s take a look at the top IP scanner tools used by system administrators, network engineers and penetration testers.
1. Nmap IP Scanner
We can’t put any other tool in the number 1 spot. Nmap has been and will probably remain our favorite hacking tool for infosec research tasks, and that includes IP scanning as well.
We’ve written about Nmap before, back when we explored the best port scanners and showed how easy it is to scan any host when you’re seeking critical information such as open ports, OS version, and other pertinent details.

What many people don’t realize is that Nmap is the perfect tool for a network IP audit. So let’s use some Nmap commands and begin the process of discovering all the servers behind the network.
Here, we’re going to skip all port scans, using an option called “skip port scan”:
This is the expected output:
As you can see, no port scanning has taken place—instead we used Nmap to ping hosts and get a response from each one of them. This type of IP scanner feature is also called “ping sweep” or “ping scan”.
Performing this same scan on an Internet-connected server can yield a lot of interesting results.
Nmap can be installed in CentOS/RHEL and other Red Hat-based distros by using:
If you’re using Ubuntu/Debian, then this should do the trick:
Stay in the loop with the best infosec news, tips and tools
Follow us on Twitter to receive updates!
2. ARP Scan
The ARP Scan Tool is another great resource for creating a full IP address map of any network. Arp-scan is quite useful for discovering all hosts within a specific network, even those that are protected behind firewalls.
Installing this tool in Red Hat-based systems merely requires you to run:
Same for Debian/Ubuntu-based distros:
To perform an IP scan with this IP scanner tool, you’ll need to run the following command:
This is the expected output:
If you’re working with a wireless network, you can also specify the type of network to scan by using:
This will let arp-scan scan the interface wlan0; you can replace that with your real interface name. Here’s a quick example:
3. Angry IP Scanner
Angry IP Scanner is one of the most popular IP address scanner tools available. It isn’t command line-based, but GUI-based instead, letting you scan your network from a fancy visual interface. You’ll be able to scan IP addresses to detect live hosts, and at the same time gather critical information about each one of them.
The only requirement to make it work in Linux is having Java installed, which is easy in most distributions.
Installation on Linux can be performed by downloading the pre-compiled packages from this link¹
Then install Java and the RPM or Deb package, as follows:.
CentOS/RHEL/Fedora:
Ubuntu/Debian
Once you’ve launch it from your desktop, you’ll see an easy-to-use interface that will allow you to scan IP ranges quickly, as shown here:.
4. Advanced IP Scanner
Advanced IP Scanner lets you scan your LAN and Wi-Fi network and give you real time information about all the connected devices. Apart from finding live hosts, it will also provide port scanning information, letting you build a complete IP address map of your entire network infrastructure.
Advanced IP Scanner features include:
- Easy-to-use interface
- Mac address detection
- Fast network scanning speed
- Can be run over remote desktop
- Exports results into CSV format
- Multi-platform support (Windows, Mac OSX and Linux)
Scanning an IP range is pretty easy: just launch the program, specify the range you want to scan and hit the Scan button. It will show you how many live hosts are found, as well as IP address, device description and assigned Mac address, as you see below:
You can download this app from the official website.²
5. ARP command
Arp command³ is one of the most useful networking commands every network engineer, sysadmin and pentester should know about. Surprisingly, not all professionals are aware of this simple yet powerful command.
That’s why it’s nabbed the fifth spot in our list of the top IP scanner tools. ARP stands for Address Resolution Protocol, and is used to display or modify the kernel IPv4 network neighbor cache.
How does it work? Simple, just pass -a option to display the full list of all known IP addresses found in your local network. You’ll also be able to detect the exact ethernet device associated with all the IP addresses.
This test was run in a real cloud server and it’s super easy to find the IP neighbors from your own network. Here, a little blur-effect has been applied to hide the real hosts and IPs, but this is pretty enough to show you the hidden power behind the arp command as IP scanner tool.
6. Fping
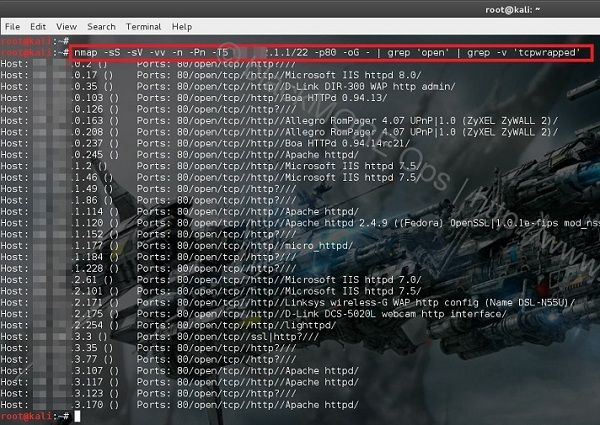
Fping is a popular IP scanner tool, but for more than “scanning,” this IP mapping tool was created to improve the old-fashioned ping command (although it’s somehow different). Fping utilizes ICMP echo requests to check if a remote host is live or not. Unlike the classic ping command, fping can be run against a large number of hosts and IP ranges. And that’s why so many system administrators and network engineers have chosen it as the perfect tool to quickly check how many hosts are live within a specified network.
You can pass several IP addresses or ranges, or make fping parse a text file and launch the ICMP echo request against each one of the listed IP addresses, or IP-range, as well as subnets.
Installation of fping on CentOS/RHEL distros:
For Debian/Ubuntu-based distros simply run:
How can you use it? Easy, just type:
That’s against an entire IP range; you can also specify a single IP instead.
At the end, it will display several useful stats about the results:
7. SecurityTrails IP Scanner
Classic command line tools are great, as well as others that include visual interfaces, but they often come with disadvantages when you’re using them to scan remote networks. There’s actually a better way to do it, without the risk of getting blocked by firewalls or IDS.
Our SecurityTrails products involve IP exploration as the #1 basic feature, when you need to know the IP address of any domain name, when analyzing the open ports of an IP address, or when you need to get the associated domains or IP neighbors of any IP address.
That’s why it’s easy for us to show you all the information you need for a specific IP address. Let’s take a look:
You can also explore IP neighbors by clicking the ‘IP Neighbors to 8.8.8.8’ button. This option will display all the IP neighbors for the specified IP address, as shown in this screenshot:
Our free app and manual IP lookups will help you get IP scan results in seconds; however, when you need to automate the entire process, you’ll need the power of our SecurityTrails API.
Performing an IP scan with the SecurityTrails API
If you’re a developer or you’re working with a team of developers in your organization, you can take advantage of our IP scanning features and integrate this into your own applications.
For this goal, we offer the X endpoint, which will allow you to retrieve IP information within seconds by querying our intelligent API. This can be done with a simple request against our HTTP-based query system, using any client—such as curl, for example:
Just replace “your_api_key” with your real API key.
You can also integrate this with many popular programming languages like Python, Javascript, NodeJS, Go, PHP, etc. Here’s an example with Python:
SurfaceBrowser Total IP Blocks
If you want to take another step forward with access to the full IP blocks of any company, SurfaceBrowser™ is the perfect tool for your IP scanner tasks.
Let’s see how you can get the full IP address space of any organization within seconds.
As shown, you’ll get the total IP blocks for facebook.com in a single place. This includes a few summaries that reveal information ordered by the regional registrar.
In this case, the RR includes records from: ARIN (105), AT&T Bell Laboratories (50), RIPE NCC (35), PSINet (25), APNIC (18), AFRINIC (2).
You’ll also be able to get the full IP stats by IP subnet size, as well as the full information for each IP block, including IP count, unique user agents, RIR, hostnames and number of associated domains.
Once you’ve finished locating all the IP blocks you need, you can explore any of the blocks by clicking the IP and its subnet, where you’ll find details such as IP count, bitmask, base IP, broadcast IP, mask, host mask, service provider like ASN, organization and company behind this network.

Conclusion
Clearly, there are a lot of IP scanner tools from which you can choose. Managing a large IP space can be quite complex if you’re not relying on any of them.
If you’re part of the infosec community, an IP scanner toolkit could be your best asset for automating your OSINT and intel-reconnaissance tasks.
Take safety and security to the next level: automate all your IP address exploration by using our powerful API. Sign up today for a free API account or book a demo with our sales team to test SurfaceBrowser™, our enterprise-grade product that will reveal the entire attack surface area of your company, including all of its IP address space.
¹ https://angryip.org/download/#linux² https://www.advanced-ip-scanner.com³ https://www.cisco.com/c/en/us/td/docs/routers/crs/software/ip-addresses/command/reference/b-ip-addresses-cr-crs/b-ipaddr-cr-crs_chapter_010.pdf
Hacking An Ip Mac Binding Video
Esteban Borges is a security researcher and technical writer specialized in Linux security. He has been working in the cybersecurity industry for more than 15 years, with a focus on technical server security and open source intelligence.
Get the best cybersec research, news, tools,
and interviews with industry leaders
Dealing with Duplicate IP addresses
© April 2009 Anthony Lawrence
Duplicate IP's on a network is an interesting problem that has no completely satisfactory solution, especially when malicious intent is involved. Let's leave those intentional conditions for another day; here we'll look at what happens when an IP gets duped accidentally.
The 'accident' can be from a human assignment of a static ip that was already in use. It can come from setting up two DHCP servers with overlapping ranges. It can come from a machine that legally obtained a DHCP address at some time in the past but has been shut off for sometime since then and that IP has been reused for some more active machine.
The cause can also be a smart switch or incorrect assigment of MAC addresses.
Whatever the reason, there is the very important question of how this affects other machines on the network. Ideally, a machine that starts up with an address already in use elsewhere should notice that and shut its network down. Unfortunately, not all network software is so friendly and polite.
However, being polite can be frustrating if the machine demurring to use an address is the machine that is supposed to have that ip. Maybe it's a server or printer that was down for maintenance and upon its return to the live network some squatter has stolen what used to belong to it.
Finding a squatter
In that case, you need to track down and nullify the impersonator before you can get the rightful device back in service. One way is to look at its MAC address as shown in the arp cache. If you are really lucky, looking up that MAC will point to something that you can easily identify. If not, 'nbtstat' (Windows) or 'nmblookup' (Samba) could give you a machine name. If it doesn't, or if machines are named in the haphazard fashion most typically done, your best option (assuming you don't have a smart switch that can help) is to start unplugging things at the switch to track it down - when the ping stops, you've found the wire. Start by disconnecting whole switches to isolate where it is and then zero in on it. Unfortunately, in places that never bothered to number jacks, you may still find yourself running around with a probe even after you have found one end of the wire. At least you know you can ignore the folks still browsing the Internet..
Speaking of finding the offending machine: I've seen a Windows server get confused by itself. That is, for some reason it sometimes thought it was seeing its own self on the network and would complain about the 'duplicate' IP. I think this happened because of a name change, but I never did get to the bottom of it and a new server replaced it soon after..
Which device gets the traffic?
If neither OS is willing to play nice and not use the IP in conflict, the question then becomes which of these two devices will be seen by the rest of the network? A machine that has previously cached the MAC address of one of the devices will continue to talk to that, but otherwise its a coin flip: who answered the arp request first?
That leads to one way to prevent IP confusion: hard code the arp cache for machines that simply must not be confused. If you have a client box that has a really critical need to talk to ServerOne at its ordained IP address, hard coding the arp cache on the client with the server's MAC address will keep it faithful - well, at least from most accidental impersonations. Something still could spoof the MAC, but that's usually going to be purposeful rather than accidental.
That hard coding of the MAC can also be done at an intelligent switch. Some switches allow port-ip binding - locking an ip to a specific port on the switch. Doing both of those things would go a long way to ensuring that packets are going to the right device, but of course would also make your network harder to maintain. No more just plug and play, there'd be procedures and paperwork for that. The extra trouble might be well worth it in some scenarios but nothing and an annoyance in others.
In some situations you might need to bring together whole networks with overlapping IP's - that's a job for a NAT router.
Hacking An Ip Mac Binding Free
You can't really prevent duplicate IP's. You can detect duplicates, block them, perhaps even mask them, but there's always a price to pay somewhere.
Some links you might find useful:
Mysterious Duplicate IP problem solved
New Dell machine kills server
Detection of duplicate IP addresses by Microsoft TCP/IP
How to Troubleshoot Duplicate Media Access Control Address Conflicts
Configure Port-IP Binding
Use DHCP Snooping and ARP Security to Block ARP Poisoning Attacks
Layer 2, Mac Addresses, ARP, and Duplicate IP Detection (Linux Kernel Patch)
Got something to add? Send me email.
(OLDER) <- More Stuff -> (NEWER) (NEWEST)
Printer Friendly Version
-> -> Manage duplicate ip address conflict
Hacking Through Ip Address
Hacking An Ip Mac Binding Tool
Inexpensive and informative Apple related e-books:
Take Control of Preview
Are Your Bits Flipped?
Take Control of Automating Your Mac
Take Control of Pages
Take Control of the Mac Command Line with Terminal, Second Edition